A Blueprint for Digital Identity
The digital economy requires new approaches to user identification, and financial services firms are positioned to lead the way.
User identification is a vexing problem for financial services firms. It’s at the center of many processes, including payments and loans, and both detail and accuracy are critical. But establishing identity today means either collecting physical proof—by scanning a driver’s license, for instance—or relying on the “know your customer” approach. Neither fulfills the requirements of a digital future.
Meanwhile, the need for a digital solution to identification is becoming urgent. Online transactions are growing in volume and complexity. Customers across industries increasingly expect seamless, omnichannel service delivery. Regulators are demanding greater transparency in transactions. And hackers can exploit weak identity systems more readily than ever, wreaking financial and reputational havoc in the blink of an eye.
It’s a problem that’s relevant in many areas today, but according to recent research from Deloitte Consulting LLP and the World Economic Forum, financial institutions are particularly well positioned to take the lead on developing a solution. They already perform many digital identity functions in the normal course of business. Their operations span multiple jurisdictions. They’re the intermediary of record in many transactions. They’re both strictly regulated and mature. Finally, they also stand to benefit from improved efficiency, increased revenues from new products and services, and even transformation into new business areas. Potential applications include tailored risk profiles, international resettlement, digital tax filing, improved risk assessments, and much more.
Done right, a digital identity network would benefit everyone involved. Collecting and sharing supporting documentation would be easier, for example. With cutting-edge authentication and security protocols, a digital identity system would make it harder to damage, lose, steal, or tamper with identification records. Digital identities would also offer customer-serving institutions a better way to know and serve their customers.
Guiding Principles
“Identity”—whether of an individual, legal entity, or asset—comprises many different pieces of information, also called attributes. The more attributes there are, the stronger the identity. For example, a Social Security number is unique to an individual, but it reveals almost nothing by itself. The person’s name and date of birth provide a bit more information. A personal photo, mobile number, residential address, school records, and work history paint a much more complete picture.
In the digital world, identity is a set of standardized digital records that represent a user. Identity providers verify and store these records, and supply them to the parties with which users transact, effectively completing transactions on behalf of the users.
A strong digital identity system will conform to five core principles:
Serve the social good. It will provide identity to all users, serve user interests, and be open to all who wish to participate.
Protect users. Current identity systems put users at risk by leaving their information vulnerable to privacy infringement, data leakage, and overexposure. A digital identity system will ensure that involved parties see only the data they need and use it only for the purposes they disclose.
Provide user control. More than one identity system has failed because users didn’t trust it. Giving users control of their data will help ensure that doesn’t happen.
Take a long-term view. Stakeholders should know their investment will pay off, so it’s important to design and build the identity system for sustainability.
Embrace openness. Finally, a good identity system will be built on open technology and data standards and designed to integrate new parties and serve changing user needs.
A Multilayered Solution
An effective digital identity system requires a multilayered solution based on standards that govern system operation. (These still need to be developed.) The top level is service delivery, which must be efficient, effective, and seamless. The layers in between include authorization, attribute exchange, authentication, and attribute collection. Each layer presents its own set of challenges (Figure 1).
Figure 1: Challenges at Every Level
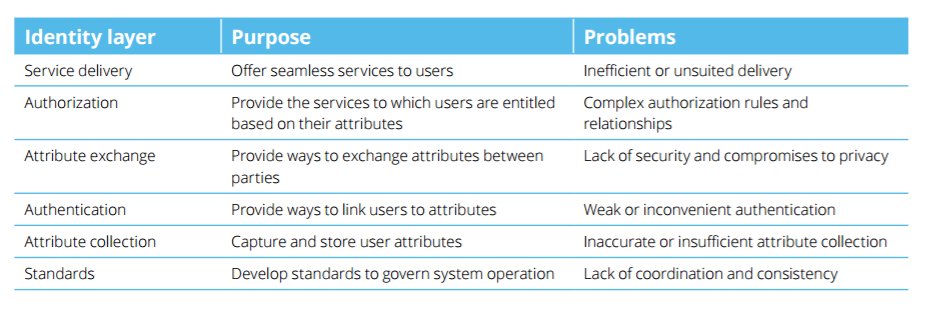
Many efforts today address only one layer. For instance, authentication technology solutions tend to rely on attributes that have already been collected. These solutions provide a better experience for users and ensure the same person is transacting each time, but they don’t help confirm that person’s identity.
Technology companies, professional organizations, and governments are carving out territory with individual solutions, but these efforts have not coalesced into an integrated digital identity system that’s secure, convenient, effective, and trustworthy.
The Road Ahead
Some promising technologies are bringing us closer to a digital identity system. Advancements in data storage, for example, offer greater privacy, security, and user control. New data transfer protocols tighten protection against interception and decryption while again putting more control in users’ hands. New authentication techniques are in development as well. These link users to their digital activities in more reliable and persistent ways.
That said, there may never be a single, global solution for identity. Different types of users have different identity needs. Individuals must be able to complete transactions safely and conveniently. Legal entities require a comprehensive way to aggregate data for managing risk. Assets need a tracking system that provides transparency around ownership and value.
Privacy needs also vary. It’s essential for individuals, while legal entities and assets can do without—in fact, privacy might even interfere with their larger purposes. Individuals act on their own behalf; legal entities and assets have custodians who act for them. Identity is also cultural. The people of some nations accept a national ID card; others don’t. And some governments may not be stable enough to carry out digital identity.
Ultimately, different groups will build their own identity networks, and that’s probably as it should be. We encourage firms to consider a bottom-up approach to digital identity. First, articulate the problem to be addressed. Test and refine the system with a critical mass of parties, then gradually scale it to include more. It’s equally important to build connectors among the separate identity networks developed. Those connections are the rails of interoperability that will allow a global blueprint for digital identity to emerge.
Source: deloitte.com, January 17, 2017